熱門話題
#
Bonk 生態迷因幣展現強韌勢頭
#
有消息稱 Pump.fun 計劃 40 億估值發幣,引發市場猜測
#
Solana 新代幣發射平臺 Boop.Fun 風頭正勁

Phylax Systems
由網路實施的應用程式定義的安全性
我們的開發關係團隊又一次做出了精彩的分析。

jacob Φ7月10日 23:31
GMX v1 Lost $42M Through AUM Manipulation
Yesterday GMX v1 suffered an attack that drained $42M through AUM manipulation. This was GMX's 2nd major hack of 2025 (lost $13M in March).
Disclaimer: This is not a full post-mortem, I've mainly looked into the AUM manipulation part.
The Attack Vector:
1. Exploited reentrancy in `executeDecreaseOrder` function
2. During callback, opened massive short positions at artificially low prices
3. Manipulated `globalShortAveragePrices`, inflating AUM calculation
4. System thought it had huge "unrealized profits" from shorts
5. Redeemed GLP tokens at inflated prices, extracting real assets
The Core Issue:
GMX's AUM = Physical Tokens + Stablecoins + Unrealized Trading Profits + Fees
When shorts lose money (current price > average price), the vault "profits" and AUM increases. The attacker exploited this to create artificial profits.
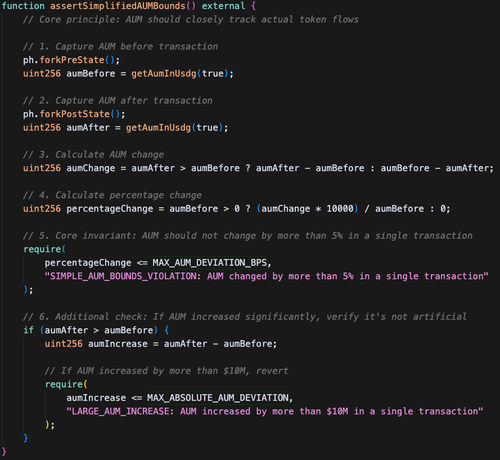
Simple Prevention:
An AUM bounds invariant enforcing `AUM_change ≤ net_token_inflow + 5%` would have caught this immediately.
The attack created massive artificial value with minimal real deposits - exactly what economic sanity checks detect.
A simplified version of a @phylaxsystems assertion that could have detected and prevented the hack:
698
熱門
排行
收藏
鏈上熱點
X 熱門榜
近期融資
最受認可





















