Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
[deleted & reposted to clarify it's a phishing attack, NOT a hack]
In the last 60 days, a phishing attack has compromised 1200+ addresses on Hyperliquid
The phishing attack works with a single signature that upgrades the EOA to a 1 of 1 multisig with the attacker as the only signer
The upgrade is immediate & gives the hacker full access to all of their assets on HyperCore (including unstaking HYPE & withdrawing after 7 days)
Multsigs are a HyperCore primitive & so the attacker does not gain access to assets on HyperEVM (only HyperCore)
Putting a spreadsheet of compromised addresses in the next tweet (ty @_Syavel_ for data)

List of 1200+ compromised addresses:
Urgent: If your address is on this list, please DM any HyperEVM apps or website you remember visiting or signing txns from so we can identify the source website or dapp ASAP
If your address is on this list, your assets on HyperEVM are safe & can be transferred to a new address
The phishing signature would only be reversible with a signature from the hacker or some sort of upgrade to the multsig primitive by the Hyperliquid team/validators
It's HIGHLY recommended to separate hot & cold wallets (particular when experimenting with new apps)
In addition, you should NEVER sign signatures that are not human-readable text. When in doubt, spin up a new wallet & use that one.
@0xBreadguy seems like it might be compromised pks actually

7.6.2025
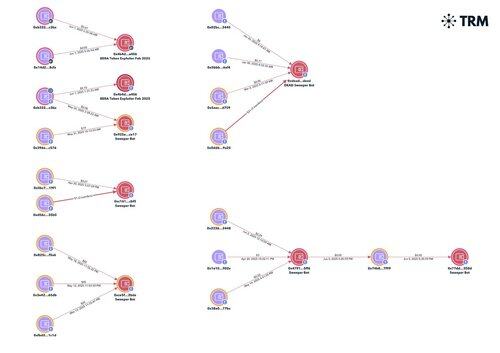
This isn't phishing🤦♀️
These private keys were previously compromised by malware. They all have their balances swept on other chains to known sweeper bots associated with MaaS / infostealer logs e.g. Raccoon, Vidar, etc.
Basically someone went thru millions of already-compromised keys, identified the ones that had Hyperliquid shit, and is sweeping those balances.
The keys were seen in logs (aka compromised) as early as Fall 2023 and as recently as Mar 2025. Most of the ones with any remaining balances are found in the more recent logs (e.g. Jan 2025) but this says more about which addresses still have a balance than it does about when the key was first compromised.
Lesson: Don't install malware, kids.
69,47K
Johtavat
Rankkaus
Suosikit













