Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
A few weeks ago, I was responding to a cybersecurity incident - $500,000 have been stolen from a #blockchain developer. The infected operating system was freshly installed, and the victim was vigilant about cybersecurity. How could this happen? New supply chain attack? [1/6]
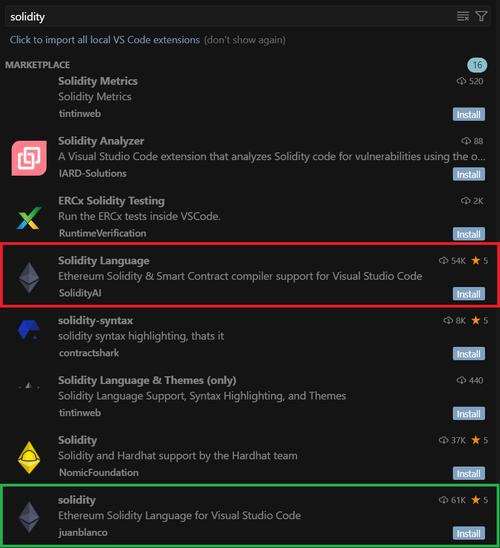
After examining the developer's hard disk, I found out that the cause of the infection was an installed malicious extension for the Cursor AI IDE. It was supposed to highlight code written in Solidity, but in reality it acted as a malicious downloader. [2/6]

But how could the infected developer, who was quite experienced, have downloaded this obviously malicious extension? It turns out that attackers have been able to make the malicious extension rank higher than the legitimate one. [3/6]
115,91K
Johtavat
Rankkaus
Suosikit