Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.

sudo rm -rf --no-preserve-root /
𝐖𝐨𝐫𝐤𝐢𝐧𝐠 𝐨𝐧 𝐰𝐡𝐚𝐭'𝐬 𝐧𝐞𝐱𝐭.
ꟼGꟼ: 063E 966C 93AB 4356 492F E032 7C3B 4B4B 7725 111F
sudo rm -rf --no-preserve-root / kirjasi uudelleen
BlockThreat - Week 28, 2025
💙 Sponsored by @SecurityOak
🔥 Mass exploitation of proxy contracts discovered by @deeberiroz and whitehatted by @pcaversaccio @dedaub and @_SEAL_Org
💸 @GMX_IO reentrancy hack $42M ($37M recovered)
💸 @KintoXYZ uninitialized proxy. $1.55M
2,42K
sudo rm -rf --no-preserve-root / kirjasi uudelleen
Lessons for security experts: Audit proxy inits rigorously.
Monitor delegatecall chains (easy to do in our app) & ensure storage integrity with complex proxying patterns.
Props go to @deeberiroz @VennBuild @pcaversaccio @_SEAL_Org
Stay vigilant.
1,99K
so I found out that it's even fancier. I observed that the frontrunning tx (by the attackers) calls `initialize` and protocols also call _successfully_ `initialize` after (thus they think everything is normal). But wait, how is this even possible? I had to look very deep into the storage slot changes and guess what I found: they _reset_ the `_initialized` storage slot value at the end of the frontrunning tx (after they swapped to the malicious implementation contract). This means that the proxy storage looks now as it was never initialised.
The relevant storage slot to look at is `keccak256(abi.encode(uint256(keccak256(" - 1)) & ~bytes32(uint256(0xff))` = `0xf0c57e16840df040f15088dc2f81fe391c3923bec73e23a9662efc9c229c6a00`
This is next-level evil.



sudo rm -rf --no-preserve-root /10.7. klo 22.13
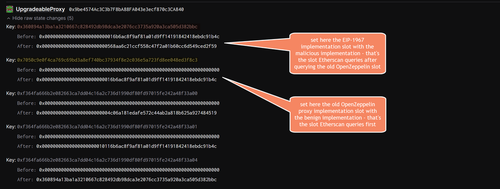
It gets even more fancy: the way Etherscan was tricked showing the wrong implementation contract is based on setting 2 different proxy slots in the same frontrunning tx. So Etherscan uses a certain heuristic that incorporates different storage slots to retrieve the implementation contract.
There is an old proxy by OpenZeppelin who used the following slot: `keccak256("org.zeppelinos.proxy.implementation")` = `0x7050c9e0f4ca769c69bd3a8ef740bc37934f8e2c036e5a723fd8ee048ed3f8c3`
We now also have the standard EIP-1967 slot `bytes32(uint256(keccak256('eip1967.proxy.implementation')) - 1)` = `0x360894a13ba1a3210667c828492db98dca3e2076cc3735a920a3ca505d382bbc`
So what happened is that the old OpenZeppelin proxy slot was written to with the benign implementation address _and_ the standard EIP-1967 slot was also written to with the malicious implementation address. Since Etherscan queries first the old proxy slot, it retrieved the benign looking one first and thus displayed it.
21,57K
sudo rm -rf --no-preserve-root / kirjasi uudelleen
Earlier this week, a potential vulnerability in Orderly’s cross-chain manager contract on BNB chain was identified.
In response, our BNB vault for deposits and withdrawals was immediately paused, contracts were migrated and deposits/withdrawals resumed within 2 hours.
✅ No user funds are at risk, or were lost.
Special thanks to @deeberiroz, @VennBuild, @seal_911, @pcaversaccio, and the rest of the team who helped flag this!
Safer together 🤝
7,54K
sudo rm -rf --no-preserve-root / kirjasi uudelleen
[5/5]
Gratitude roll-call • @SlowMist_Team for nonstop triage & patching • @dedaub, @pcaversaccio, and the @seal_911 war-room for a 36-hour code sweep • @etherscan for lightning-fast UI cleanup • And again, thank you @deeberiroz, @VennBuild, @davidberiro—your heads-up saved the day 💙
12,32K
It gets even more fancy: the way Etherscan was tricked showing the wrong implementation contract is based on setting 2 different proxy slots in the same frontrunning tx. So Etherscan uses a certain heuristic that incorporates different storage slots to retrieve the implementation contract.
There is an old proxy by OpenZeppelin who used the following slot: `keccak256("org.zeppelinos.proxy.implementation")` = `0x7050c9e0f4ca769c69bd3a8ef740bc37934f8e2c036e5a723fd8ee048ed3f8c3`
We now also have the standard EIP-1967 slot `bytes32(uint256(keccak256('eip1967.proxy.implementation')) - 1)` = `0x360894a13ba1a3210667c828492db98dca3e2076cc3735a920a3ca505d382bbc`
So what happened is that the old OpenZeppelin proxy slot was written to with the benign implementation address _and_ the standard EIP-1967 slot was also written to with the malicious implementation address. Since Etherscan queries first the old proxy slot, it retrieved the benign looking one first and thus displayed it.

41,07K
Idk man but the real threat to Ethereum isn't the state actually (at least not today). It's the VCs & protocol careerists trying to neuter it into a shiny fintech playground for "safe", compliant DeFi. Hear me out: They don't want unstoppable code. They don't want resistance. They want fucking _control_. Because deep down, they know what Ethereum could become if it's left unchained: a censorship-resistant, privacy-first global execution layer that no state, no corp, no cartel of suits could ever fucking stop. Let's make this a reality.
19,4K
So someone contacts you on LinkedIn with a promising job opportunity. Sounds nice, innit? They seem legit (after checking them for 1 min) and after some short convo they send you a GitHub repo with a simple Next.js "recruiting task". You clone it, run it… and 10 mins later, your device is fully compromised as you find out that your hot wallets were drained. Ok, what happened? Given the fact that we (= SEAL 911) have seen this attack over and over again, let me disclose some of the most important details:
- first, the most important caveat: do NOT run random code some random dude sent you. Honestly, fucking don't.
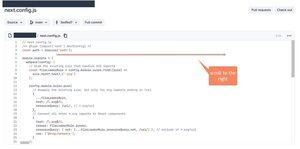
- check always the _executable_ config files of the repos thoroughly. In this particular case, the `next.config.js` file had a large padding hiding the malicious payload far to the right.
- always scroll horizontally - just because you don't see anything malicious when you look at the content doesn't mean it's clean.
Important: Malicious code can be hidden within files you trust, just not where you expect it.
I really hope this tweet reaches enough people to prevent at least a few future victims from falling for this kind of attack.


34,46K
Johtavat
Rankkaus
Suosikit
Ketjussa trendaava
Trendaa X:ssä
Viimeisimmät suosituimmat rahoitukset
Merkittävin
















